Let’s understand ledgers which form the basis of blockchain implementation. A ledger is a document which records summarized financial information as debits and credits, and shows the current balances.
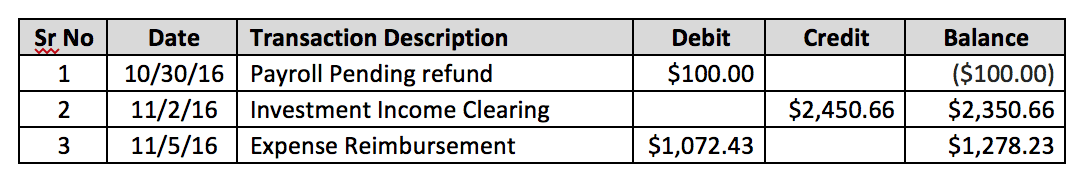
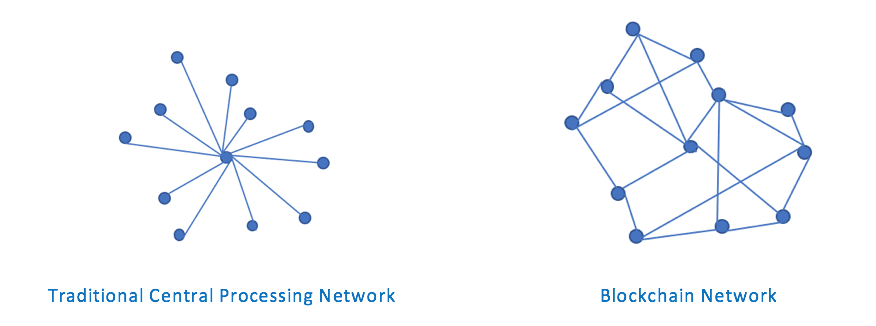
A traditional ledger entry looks like below. In the current world, companies usually store this ledger at a centralized location – following a Client / Server Architecture
There are many challenges with the current way in which these traditional ledgers work. When transferring assets, usually a third party is involved. The involvement of third part not only introduces a heavy fee, but also leads to delays. Since these ledgers are centralized, not all parties have visibility into such transactions, and thus the process is very opaque, and susceptible to frauds. Also, the client server architecture is not as robust.
Blockchain is a technology which records movement of assets from one entity to another, and every such movement is called a transaction. When such a transaction occurs, an entry is made into a ledger, recording this movement. A series of related transactions are stored in a block.
Blockchain maintains a distributed digital open ledger system, which records a series (chain) of such blocks, the asset usually being digital coins / virtual currencies / smart contracts, like Bitcoin, Etherium, etc. This ledger is maintained on multiple peer nodes in a network.
All this is achieved using a combination of 3 technologies:
Peer-to-Peer networking:
- Blockchain maintains an open ledger, which means that anyone in the network could send new transactions, and create new blocks. The ledger records all the transactions, and is essentially stored on the member nodes in the network. Each peer in the network maintains a full copy of this ledger.
- The ledger is not centrally stored thus blockchain does not rely on a single central authority, and therefore not presenting a risk of a single point of failure.
- A few systems, which follow such an architecture today are Skype and BitTorrent
Asymmetric Cryptography:
- This cryptographic system uses a pair of keys – public and private keys, to encrypt and decrypt the data. These keys are merely numerical values, which are paired together.
- Public Key is usually shared with everyone, with whom, the user would like to communicate. Private Key is known only to the user, and is not disclosed to anyone else. This empowers other users to encrypt a message, using the receiver’s public key. However, the message can be read only by the receiver, since the receiver alone has the private key, to decrypt the message.
- In blockchain, asymmetric cryptography is used to create a set of credentials for your account, to ensure that only you can transfer your tokens (Bitcoin / Etherium), and only the intended recipient receives it.
Cryptographic Hashing:
- A digital media or a group of digital media when put through a hash function generates a fixed length value (hash value), which uniquely represents that data. If one changes even a single bit in the input (digital media), the hash output is completely different from the original one. Thus, this hash value calculated on the input is used as a digital signature
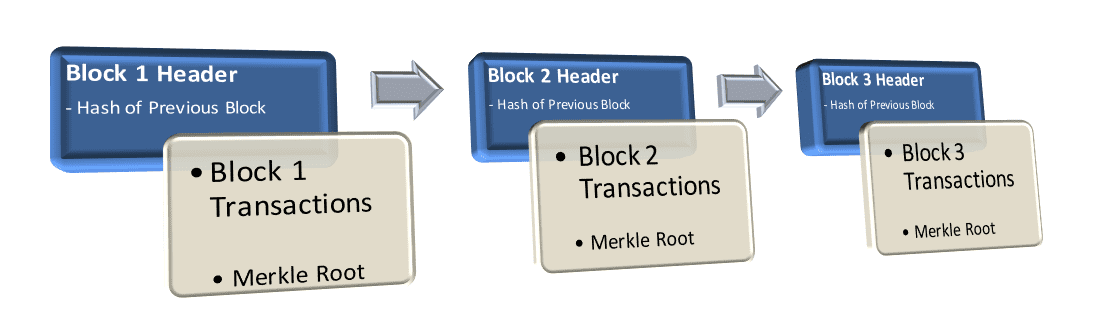
Blockchain itself is a data structure, and its data can be stored either in a file or a database. It is an ordered linked list of blocks of transactions, where each subsequent block maintains a link (hash) of the previous (parent) block. Each block in the chain has a unique hash, which is computed by the node on the basis of contents of the block.
The block consists of a header and data about transactions. For the set of transactions in a block, hash values are generated and stored in a Merkle Root for the block. If the contents of a block change even by a bit, the hash value of the block changes.
Merkle Root is the root of a Merkle tree or a Hash Tree. Merkle tree is a tree in which every non-leaf node stores the value of hash of hash of its child nodes. The leaf nodes contain the actual transactions. Hash trees allow efficient and secure verification of the contents of the block data, and are essential for the integrity of the data. It allows to track if there are any changes done to any transaction within the block of the tree, by regenerating the hash and comparing it with the original hash.
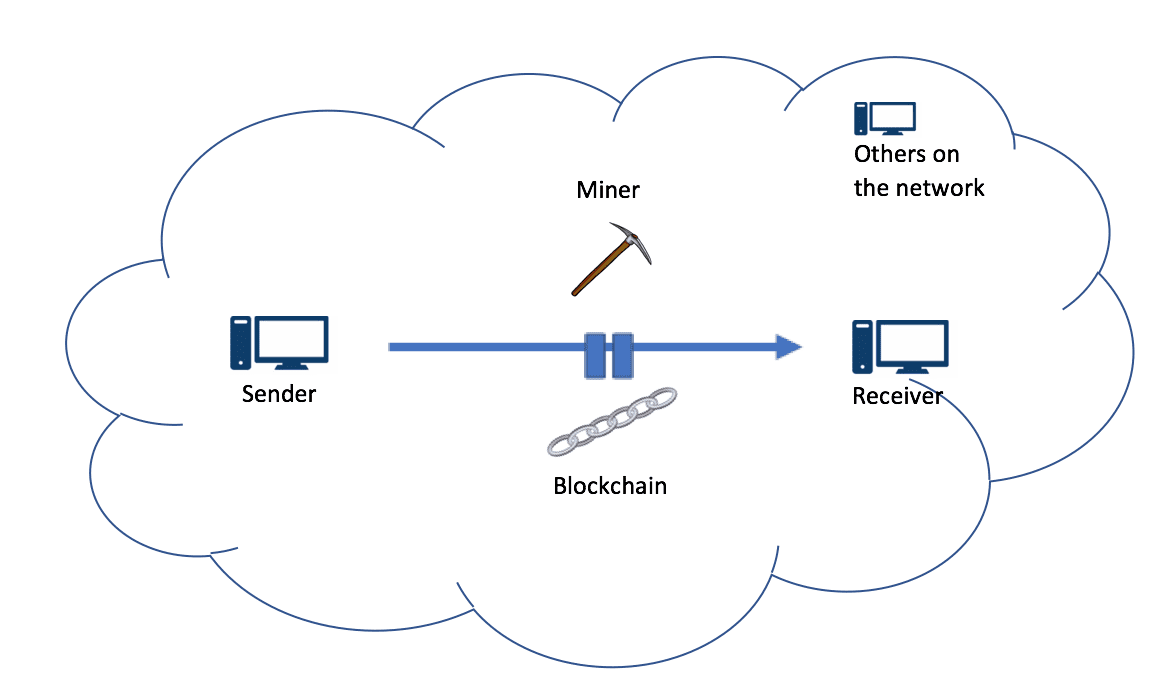
When new transactions are digitally signed, and submitted in the network, there are special nodes called miners, which confirm the validity of the transactions, bundle them in a block, and add it to the blockchain. This block then gets propagated to the network. The miners are required to solve a “proof of work” problem, which requires very heavy computing. In this, the miners are required to guess a number, which when crunched with the rest of the block data, computes a hash that is smaller than a certain number. That number is related to the ‘difficulty’ of mining, and essentially translates to the total network processing power. As more and more computers join in to mine, the difficulty level gets harder, in a self-regulating cycle.
Whichever miner is able to find the solution, gets to add the block to the chain, and in turn gets rewarded with the virtual currency. This process of adding blocks to the blockchain network is called mining.
A blockchain network could be Public or Private. In a public network, anyone in the network can read, write, as well as mine the blockchain. Security model is based on “proof of work”. In a private network, the participants are known and trusted, and the ledger is open only to the nodes in the private network.
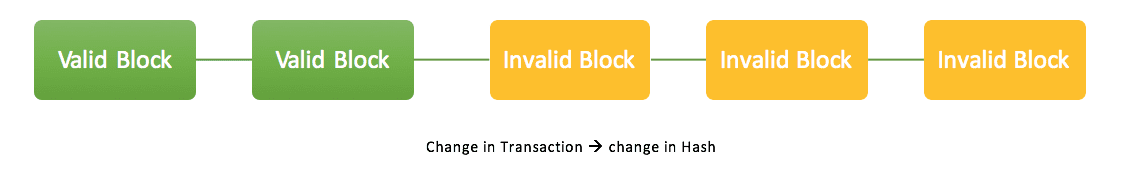
Though there is a common belief that the history in blockchain is immutable, in reality, it is not the case. Once the contents of a block changes even by a bit, a new hash is generated for that block. That new hash is always different from the original hash. The subsequent block which still holds the original hash of the previous block, now has a broken link, and thus the chain is broken.
The fact that the regeneration of the same hash for that block is extremely hard, thus re-writing parts of the invalid Blockchain will take a very long time. Once done, one would also be required to sync up with the rest of the growing network. This is what makes the history secure and almost immutable.
Blockchain is still evolving and there are newer better versions of its implementation coming up – like Etherium is an improved version of Bitcoin. There is a lot of potential for Blockchain, and companies are already exploring on how best they can leverage this technology.