
How much did it cost an identity thief in 2022 to buy some of your personally identifiable information (PII)? PrivacyAffairs.com reported that a thief could buy a compromised credit card number along with its three-digit security code for as little as $15. Similarly, a fraudster could buy a hacked Gmail account for $65 in 2022, or a hacked Coinbase verified account for $120.
According to the same source, the ability to launch a distributed denial of service (DDoS) attack on an unprotected website costs only $10 for an hour’s worth of up to 50 per second requests via the Dark Web. Imagine that—DDoS Attacks have become available as a Service (DDoSaaS, in XaaS terms).
Example sensitive data law enforcement actions in 2022
Some organizations were fined in 2022 for violating the requirements of the California Consumer Protection Act (CCPA). Most notable among these was French multinational cosmetics retailer Sephora, which allegedly sold online user PII to third-party ad networks and analytics providers without disclosing the practice to users. Sephora agreed to a $1.2 million fine in August, without admitting liability.
Sephora allegedly used third-party cookies to track user behavior across websites without user consent. Moving forward, it will provide the necessary disclosure to users, as well as detailed compliance assurance reporting to regulators.
California will begin to enforce a stricter privacy law called the California Privacy Rights Act (CPRA) in January 2023. The CPRA requires the person or organization requesting to collect sensitive personal information (SPI = passport number, Social Security numbers, or other correlatable identifiers, for example) to state the purpose and gain permission before obtaining this sensitive identity information.
In December 2022, authorities in London, UK and Malmo, Sweden arrested four men on behalf of the US Internal Revenue Service suspected of identity theft and transnational wire fraud. The men allegedly hacked into corporate systems and stole identity data in order to file false tax returns and take the refund money.
These are typical of the kinds of data privacy violations that have become more and more numerous over the past year.
The root problem with online identity: Poor data architecture design
Law enforcement does not have a lengthy list of successful prosecutions against identity thieves, for reasons that are understandable. Imagine the challenge of collecting solid evidence against people halfway around the world, at least some of whom can do the digital equivalent of shapeshifting.
Unfortunately, the data that thieves seek ends up in a lot of different places. At the same time, there are huge amounts of structured, sensitive personal data in centralized repositories managed by retailers, governments, credit scoring bureaus and many other kinds of organizations.
Sensitive data duplication and losing track of where you’ve stored this kind of data is common in today’s organizations. Semantic Arts’ Dave McComb noted in 2021 that one of his banking clients had customer US Social Security Numbers (unique government IDs banks typically use to authenticate the customer’s identity and control customer access to the system) stored in over 8,000 different places.
It was not unusual for this sensitive personal information (SPI) to be in duplicate form in different places in a bank’s databases, he said. What was surprising was the sheer number of duplicates in this case. This very high number was clearly a red flag indicating that the bank had long ago lost track of its data.
SPI that companies mindlessly duplicate and then lose track of in this way is a key indicator of a lack of data maturity. Data that’s oversiloed, disconnected, and not designed to be discoverable eventually becomes a neglected mountain of risk, rather than information.
Identity proofs (a.k.a., verifiable credentials) that stay encrypted and on your phone
Given a dearth of successful enforcement efforts,
Organizations you do business with have a standing need these kinds of proofs:
- You are who you say you are
- You do have certain qualifications, such as
- A driver’s license to be able to drive legally and provide proof of age
- A diploma or other educational institution’s certificate of course completion requirements for employment, or
- Proof of employment and a stable income to be able to borrow
- Proof of citizenship and associated proofs to cross national borders, etc.
- Verifiable elements of health records that hospitals, clinics and doctors’ offices continually collect and recollect
Fortunately, many countries and transnational governments in the next few years will be encouraging the use of digital wallets and infrastructure made to their specifications available using open standards. Central to the functions of these wallets will be self-sovereign identity, or the ability to keep your own correlatable identifiers and credentials with you on your phone or other end-user devices.
The European Union’s European ID (eID) project is a prime example of a multinational, standards-based, interoperable approach to digital wallets for credentials storage that’s in the works. In September 2022, the Nordic-Baltic eID Project (a consortium involving Denmark, Germany, Iceland, Italy, Latvia, and Norway) announced a cross-border wallet pilot. The EU plans to launch the eID system beginning in 2024.
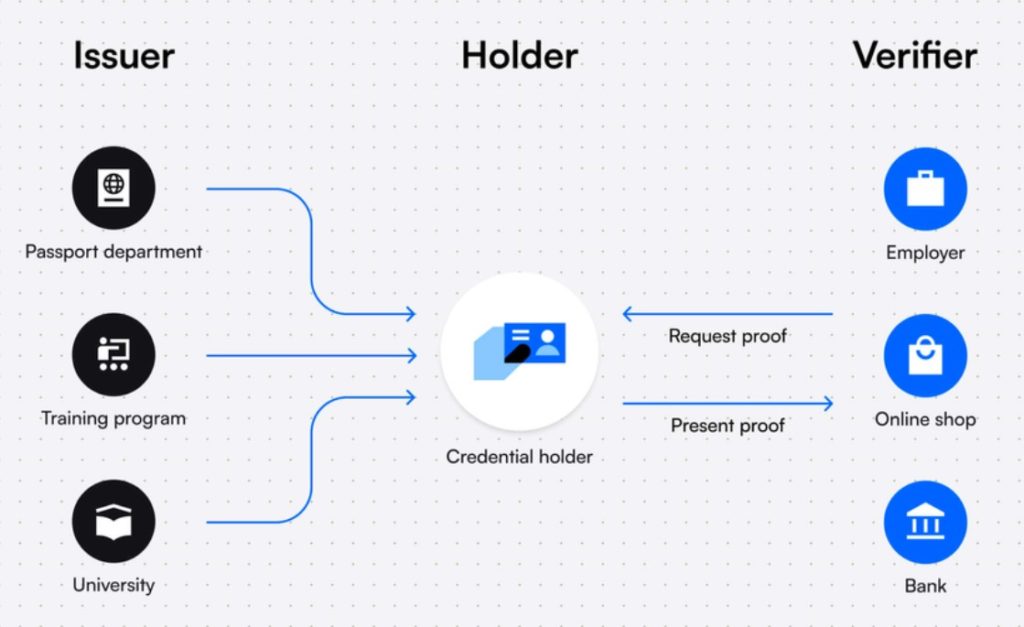
The EU and EU country governments are harnessing existing standards and creating specifications criteria for digital wallets. Commercial wallet and infrastructure providers such as CyberArk, Dock.io, and Thales Group are already supporting the decentralized identifier (DID) W3C recommendation, for example. Keep in mind that the larger identity system will include Issuers (such as a country’s passport department), Verifiers (such as a bank, other retailer, or employer), and the Holder, or user. The Holder has control over who gains verification access and visibility into messaging involving the wallet and its contents
Self-sovereign identity, despite the name, depends on two other roles besides the identity/credential holder to participate in the network.
Now that the latest tulip market speculation phase of cryptocurrency trading is behind us, 2023 could be the year when self-sovereign identity finally gains a foothold.
